Category: General
-
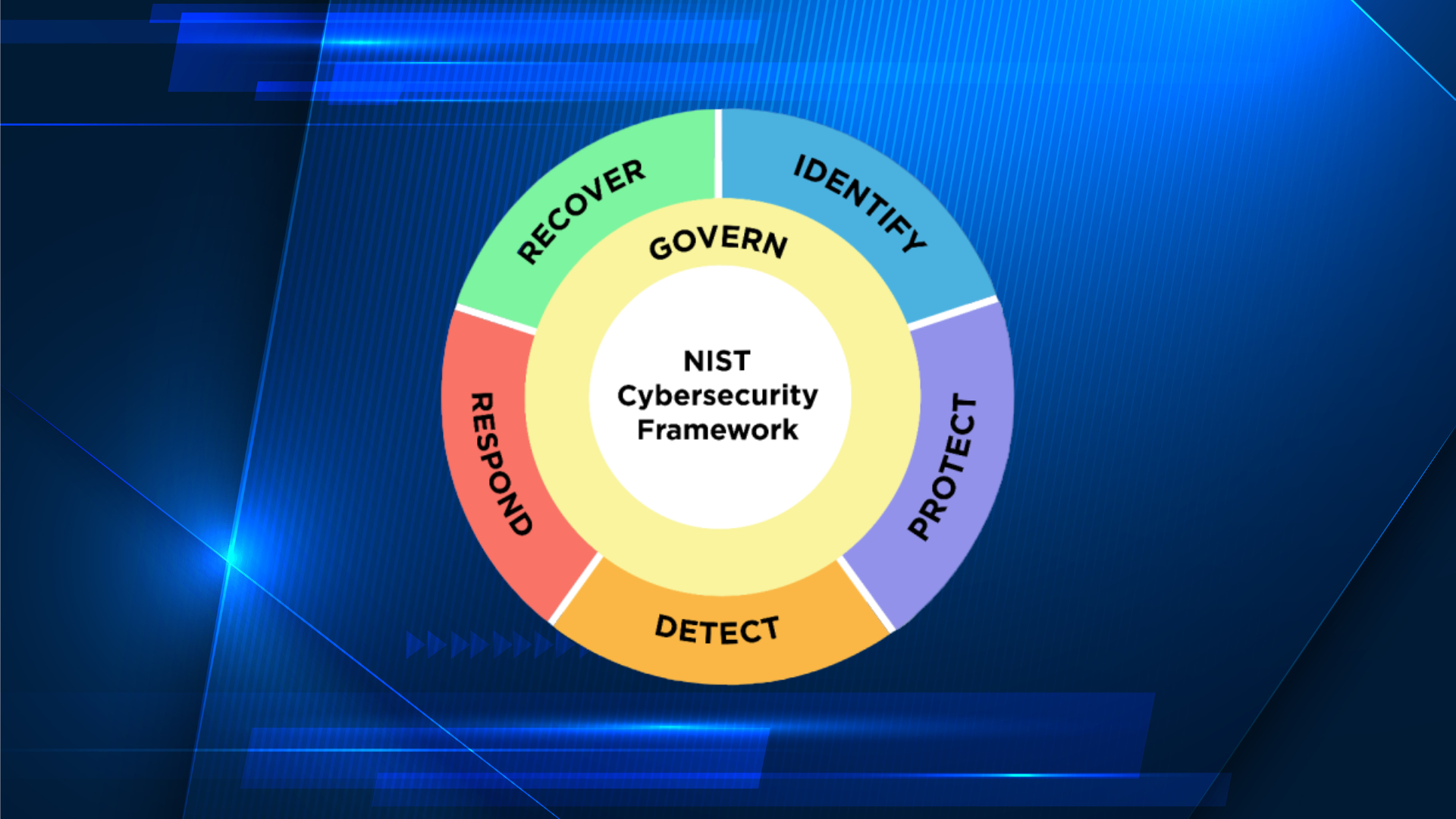
A structured approach to cybersecurity is essential
A structured approach to cybersecurity is essential in 2025 due to the constantly evolving and increasingly sophisticated cyber threat landscape. Here’s why: In summary, a structured approach to cybersecurity is not just a best practice, but a necessity in today’s digital world. It provides a roadmap for building a robust security posture, protecting your organization…
-

Black Box vs. White Box Penetration Testing
Penetration testing, often called ethical hacking, is a crucial security practice that simulates real-world cyberattacks to identify vulnerabilities in a system. This process helps organizations understand their security posture and proactively address weaknesses before malicious actors can exploit them. A key aspect of penetration testing lies in the level of information provided to the testers,…
-

Zero Trust: A Modern Security Imperative
In today’s interconnected world, the traditional “castle-and-moat” security approach, which assumes everything inside the network is safe, is no longer sufficient. The rise of cloud computing, remote work, and mobile devices has blurred the network perimeter, making it increasingly difficult to define what’s “inside” and “outside.” This shift has given rise to the Zero Trust…
-

Welcome to The Cyber Strategist: Your Guide to Navigating the Digital Landscape
In today’s interconnected world, cybersecurity isn’t just a technical concern—it’s a critical business imperative. From sprawling corporate networks to the personal devices we carry in our pockets, every digital touchpoint presents both opportunity and risk. That’s why I’m thrilled to launch The Cyber Strategist, a space dedicated to exploring the ever-evolving world of cybersecurity and…
